In a startling revelation, cybersecurity researchers have identified several apps on the iOS App Store equipped with hidden image-scanning capabilities, underlining the fact that no operating system is completely secure. This discovery comes as part of a broader malware campaign known as SparkCat, which targets both Android and iPhone users with the intent of stealing sensitive data such as images stored in phone galleries.
While previously, harmful applications were predominantly associated with Android's Play Store, the emergence of these apps on Apple's marketplace raises significant concerns. Kaspersky, the cybersecurity firm that uncovered this campaign, reported that the infected apps have been downloaded over 242,000 times by Android users, highlighting the scope of this threat. Although the exact number of iPhone users impacted remains unclear, the presence of stealer apps on the App Store is unprecedented.

This infected application was found on both Google Play and App Store. | Image Credit - Kaspersky
The malware in question utilizes an advanced Optical Character Recognition (OCR) plugin developed with Google's ML Kit library to extract sensitive text from images, specifically searching for keywords that could lead to cryptocurrency wallet recovery phrases. This dangerous capability also means it can identify other sensitive information, including messages and passwords stored in image format.

Stay informed with the latest iOS news
By subscribing you agree to our terms and conditions and privacy policy.
The SparkCat campaign targets both Android and iPhone users. | Image Credit - Kaspersky
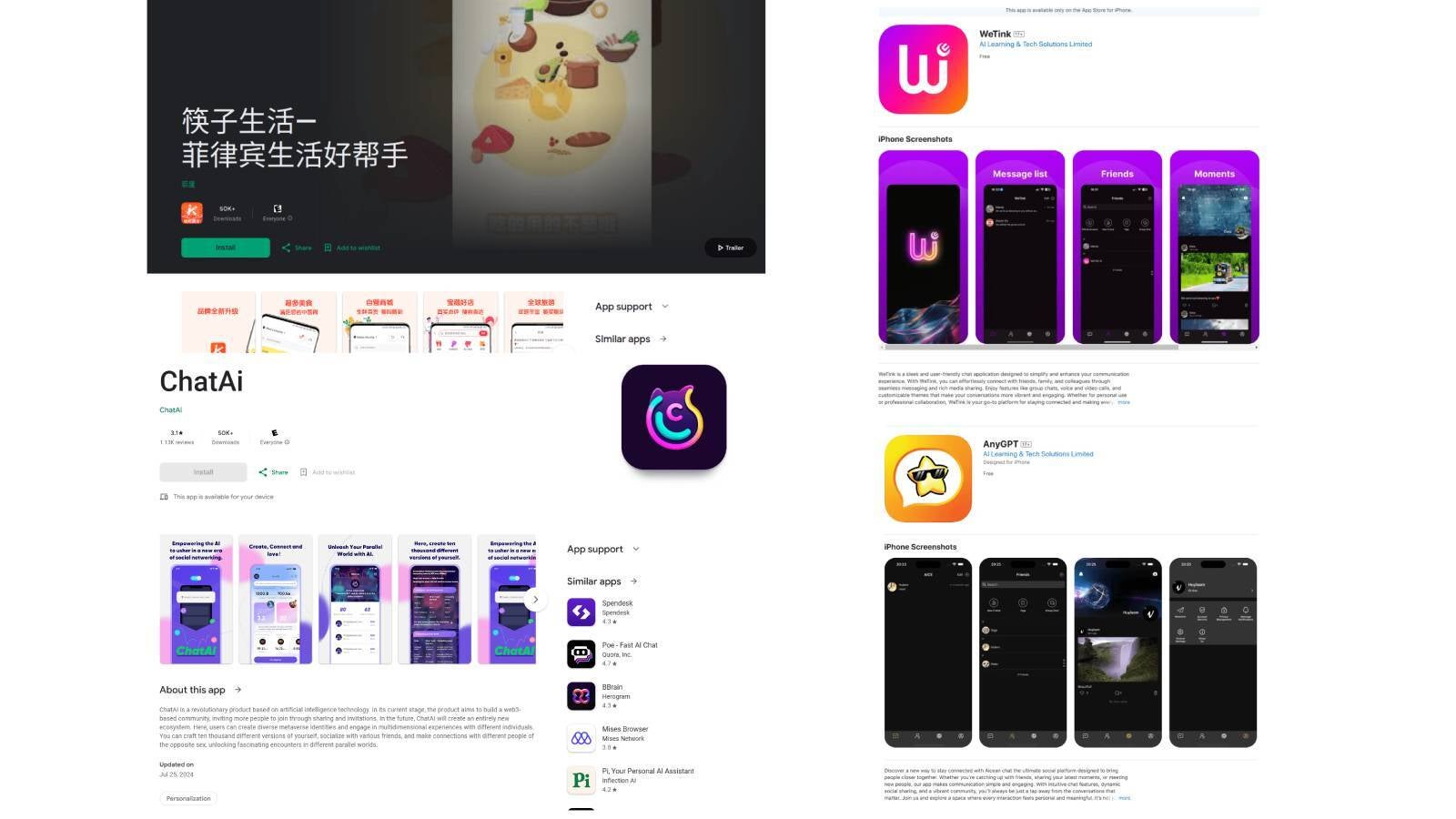
Identified malicious applications associated with this campaign include the food delivery app ComeCome, along with messaging platforms ChatAi, WeTink, and AnyGPT. Alarmingly, several of these apps remain available for download in both app stores.
Active since March 2024, this malware has proven difficult to detect, disguising itself within legitimate app functionalities and evading scrutiny by requiring minimal permissions. Kaspersky has suggested that the infection could have resulted from a supply chain attack, meaning that while some apps were intentionally created to perpetrate this scheme, others may have been compromised or misused.
Targeting primarily users in Europe and Asia, this campaign also signifies an important shift in the cybersecurity landscape, emphasizing that iPhone users must be equally wary of potential threats.
If you have downloaded any of the aforementioned applications, it is imperative that you delete them immediately. To bolster your defenses against such malware, exercise caution by avoiding the storage of screenshots that contain sensitive information in your gallery.




